The worst thing about having a phone or laptop stolen isn’t necessarily the loss of the physical object itself, though there’s no question that that part sucks. It’s the amount of damage control you have to do afterward. Calling your phone company to get SIMs deactivated, changing all of your account passwords, and maybe even canceling credit cards are all good ideas, and they’re just the tip of the iceberg.
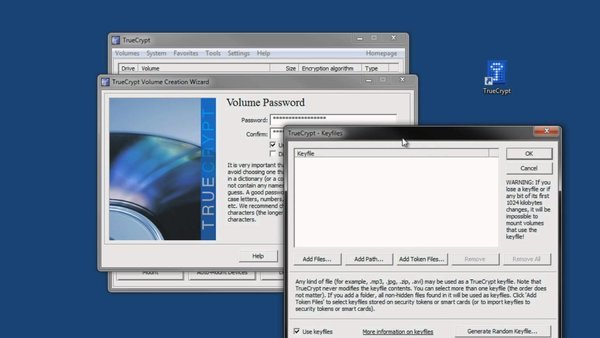
Using strong PINs or passwords and various Find My Phone features is a good place to start if you’d like to limit the amount of cleanup you need to do, but in this day and age it’s a good idea to encrypt your device’s local storage if at all possible. Full-disk or full-device encryption (that is, encrypting everything on your drive, rather than a specific folder or user profile) isn’t yet a default feature across the board, but most of the major desktop and mobile OSes support it in some fashion. In case you’ve never considered it before, here’s what you need to know.
Why encrypt?
Even if you normally protect your user account with a decent password, that doesn’t truly protect your data if someone decides to swipe your device. For many computers, the drive can simply be removed and plugged into another system, or the computer can be booted from an external drive and the data can be copied to that drive. Android phones and tablets can be booted into recovery mode and many of the files on the user partition can be accessed with freely available debug tools. And even if you totally wipe your drive, disk recovery software may still be able to read old files.
Encrypting your local storage makes all of that much more difficult, if not impossible. Anyone trying to access your data will need a key to actually mount the drive or read anything off of it, and if you wipe the drive the leftover data that can be read by that file recovery software will still be encrypted even if the new data on the drive isn’t.
There are a few downsides. If you yourself lose the key or if your drive becomes corrupted, for example, it might be more difficult or impossible to recover data. It can slow down performance, especially for devices with processors that don’t provide hardware acceleration for encrypting and decrypting data. But, by and large, the benefits outweigh the drawbacks, and the slowdown for modern devices should be tolerable-to-unnoticeable.
iOS: Don’t worry about it
As of iOS 8, as long as you set a passcode, your personal data gets encrypted. Apple’s security whitepaper (PDF) for iOS 8.3 and later specifically says that “key system apps, such as Messages, Mail, Calendar, Contacts, Photos, and Health data values use Data Protection by default, and third-party apps installed on iOS 7 or later receive this protection automatically.”
The company also claims that every current iDevice features “a dedicated AES 256 crypto engine built into the DMA path between the flash storage and main system memory,” which ought to limit the impact of this encryption on system speed.
OS X: FileVault
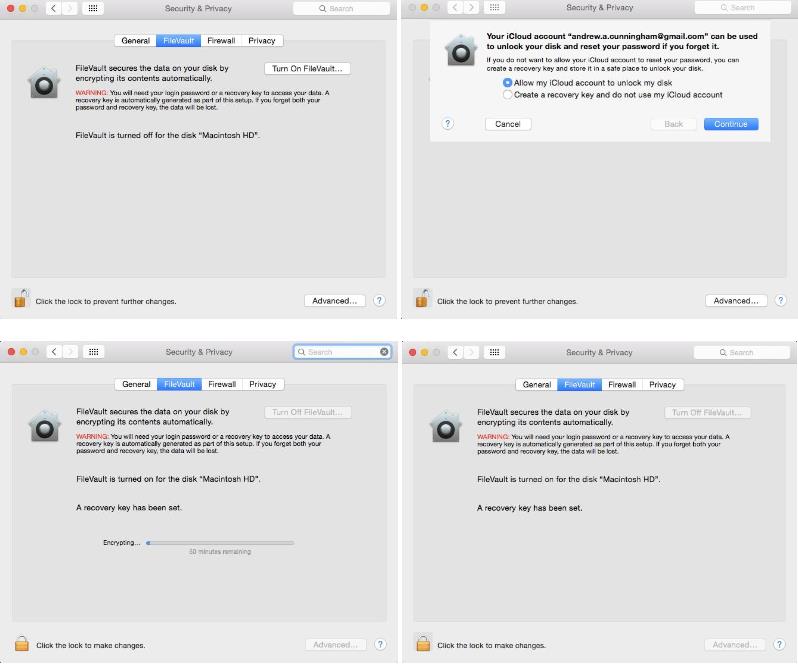
Starting with OS X 10.7 (Lion) in 2011, Apple began supporting full-disk encryption with FileVault 2. In more recent OS X versions, some Macs even offer to encrypt your storage as part of the first-boot setup process, though it’s not the default as it is in iOS.
To encrypt your drive after the fact, go to the Security & Privacy pane in System Preferences, and select the FileVault tab. Click Turn On FileVault and you’ll be offered a pair of options: store the key used to unlock your disk somewhere yourself, or choose to store it in your iCloud account. A local recovery key keeps that key off of another company’s servers, but leaves you without recourse if you lose it and you’re locked out of your system. If you do store your key in iCloud (or even if you don’t, for that matter), we strongly recommend enabling two-factor authentication for your Apple ID.
Encrypting your disk doesn’t drastically change the way that OS X works—you just need to put your account password in to unlock the disk before the operating system boots instead of afterward. You’ll also need to specify which local users’ logins can decrypt the disk. Otherwise, just the account that enabled FileVault will be able to turn the machine on. If you ever need to decrypt your Mac, it’s pretty easy if you can log in to the computer or if you have the key available.
Generally speaking, performance for encrypted devices declines less for newer Macs with hardware acceleration—most Core i5s and i7s can do it, but Core 2 Duo Macs cannot.
Android
Despite past promises, new Android devices still aren’t being encrypted by default. Default encryption is an option for OEMs, but outside of Google’s Nexus devices few if any companies are choosing to enable the feature on their phones.
You can still encrypt any relatively modern version of Android pretty easily—these specific steps work for Nexus devices or anything running near-stock Android, but the process should be similar if your phone is using a skin.
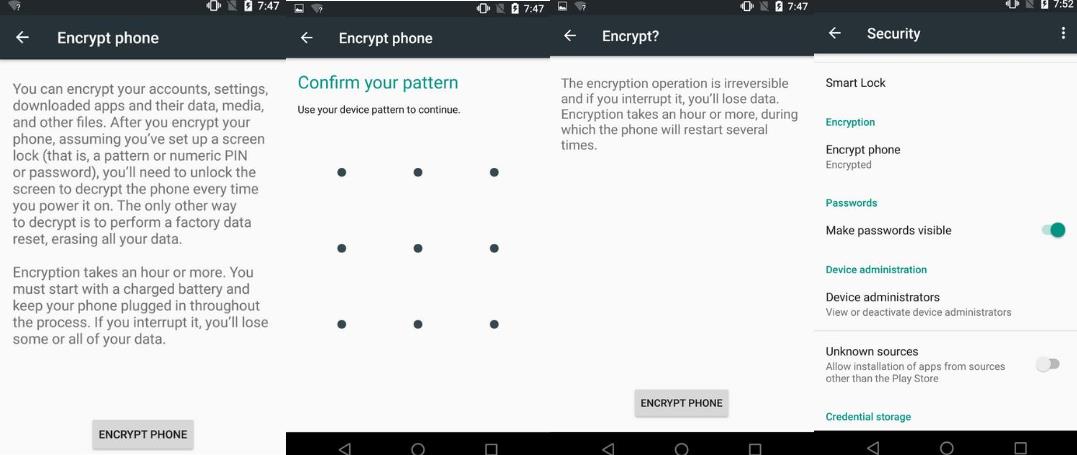
Open the Settings app, go to Security, and then tap “encrypt phone” to get the process started. Your phone may ask you to plug it in or charge the battery to a specific level before it will give you the option to encrypt, mostly because interrupting this process at any point is likely to completely corrupt your data partition. You’ll need to protect your phone with some kind of PIN or pattern or password if you haven’t already, and as in OS X your phone will probably require it before the operating system will boot.
To confirm that your phone was encrypted, go to Settings and then Security and look for a small “Encrypted” badge under the “Encrypt phone” menu item. If your phone already says it’s encrypted, you may have one of the new post-Lollipop phones that came with encryption enabled out of the box.
Depending on your phone, encrypting your Android phone or tablet can significantly impact performance. This is the worst for older or slower devices, which can use slower flash memory and filesystems and lack hardware encryption acceleration. The experience is better on newer phones with 64-bit ARMv8 processors and higher-end, faster storage.
Additionally, if you need to decrypt the device later on, there’s no way to do it without wiping and resetting the phone. If your phone came encrypted out of the box, though, there’s no way to decrypt the device without making more extensive software modifications.
Finally, in Android Marshmallow, the Android phones that include external storage are able to encrypt and protect the data on those cards as well as on internal storage.