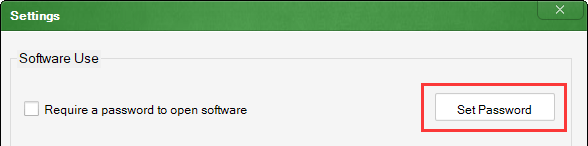
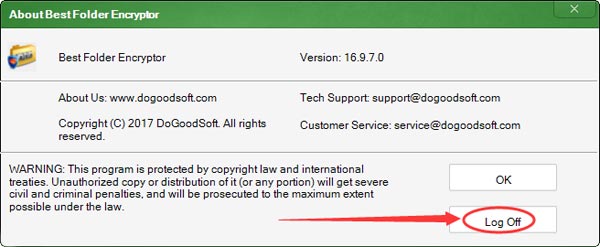
Ace Secret Disk allows you to create a secret disk on your computer, on which you can store your private files (such as photos, videos and financial information documents) just like you would do on a normal disk. In this way the danger of data leakage can be completely eradicated.
Change Log of Ace Secret Disk 8.11:
File Size: 5.74MB
Category: Encryption Software
Language: English
License type: Trial Version
OS Support: Win WISTA/Win 7/Win 8/Win 10/Win 11
Released on: Aug. 22, 2022
Download Address: https://www.dogoodsoft.com/ace-secret-disk/free-download.html
What’s New in This Version:
* Compatible with windows 11.
– No more Windows XP support.
– Included some improvements and bug fixes.
Why Choose Ace Secret Disk:
Ace Secret Disk creates an additional virtual disk on your computer with a password, which can make your private documents (images, videos, financial files, etc.) invisible and protected. It works as a regular hard disk, while completely prevents your files and folders from leakage. Ace Secret Disk is known for its three features:
(1) High Safety
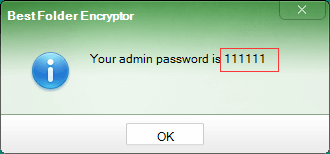
It adopts new methods to protect data on your personal secret disk, and only with the correct password you can access it.
(2) Excellent Software Performance
The secret disk takes up no extra space, with data import and export as fast as lightning.
(3) Easy and Convenient Usage
The secret disk is used just like a normal disk, easy for you to save your private files.